A cryptosystem is the implementation of cryptographic methods and the accompanying infrastructure for providing information security services. Cryptosystem is also called encryption
.
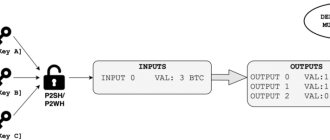
Let's discuss a simple model of a cryptosystem that ensures the confidentiality of transmitted information. This basic model is depicted in the figure below −
The figure shows a sender who wants to transmit some sensitive data to the recipient in such a way that any party intercepting or eavesdropping on the communication channel cannot extract the data.
The goal of this simple cryptosystem is that at the end of the process, only the sender and recipient will know the plaintext.
Cryptosystem components
The various components of a basic cryptosystem are as follows:
- Simple text.
This is data that must be protected during transmission.
- Encryption algorithm.
It is a mathematical process that produces ciphertext for any given plaintext and encryption key. It is a cryptographic algorithm that takes plaintext and an encryption key as input and produces ciphertext.
- Hypertext.
It is an encrypted version of the plaintext produced by an encryption algorithm using a special encryption key. The encrypted text is not protected. It flows through a public channel. It can be intercepted or compromised by anyone who has access to the communication channel.
- Decryption algorithm.
It is a mathematical process that produces a unique plaintext for any given ciphertext and decryption key. It is a cryptographic algorithm that takes ciphertext and decryption key as input and outputs plaintext. The decryption algorithm essentially reverses the encryption algorithm and is thus closely related to it.
- Encryption key.
This is the value known to the sender. The sender enters the encryption key into the encryption algorithm along with the plaintext to calculate the ciphertext.
- Decryption key.
This is the value that is known to the recipient. The decryption key is related to the encryption key, but is not always identical to it. The receiver inputs the decryption key into the decryption algorithm along with the ciphertext to calculate the plaintext.
Simple text.
This is data that must be protected during transmission.
Encryption algorithm.
It is a mathematical process that produces ciphertext for any given plaintext and encryption key. It is a cryptographic algorithm that takes plaintext and an encryption key as input and produces ciphertext.
Hypertext.
It is an encrypted version of the plaintext produced by an encryption algorithm using a special encryption key. The encrypted text is not protected. It flows through a public channel. It can be intercepted or compromised by anyone who has access to the communication channel.
Decryption algorithm.
It is a mathematical process that produces a unique plaintext for any given ciphertext and decryption key. It is a cryptographic algorithm that takes ciphertext and decryption key as input and outputs plaintext. The decryption algorithm essentially reverses the encryption algorithm and is thus closely related to it.
Encryption key.
This is the value known to the sender. The sender enters the encryption key into the encryption algorithm along with the plaintext to calculate the ciphertext.
Decryption key.
This is the value that is known to the recipient. The decryption key is related to the encryption key, but is not always identical to it. The receiver inputs the decryption key into the decryption algorithm along with the ciphertext to calculate the plaintext.
For a given cryptosystem, the set of all possible decryption keys is called the key space
.
Interceptor
(attacker) is an unauthorized entity that attempts to determine the plaintext. He can see the ciphertext and can know the decryption algorithm. He, however, must never know the decryption key.
How to find out the Windows key in ProduKey
The free ProduKey program from the well-known manufacturer NirSoft does not require installation on your computer. The application shows keys for Windows OS, Internet Explorer, Microsoft Office.
Unpack the archive with the program, and then run the “Application” file from the folder. After launch, the ProduKey utility window will display the key for the installed operating system.
Select the entry with the key for Windows 10, or another operating system, and then select “Copy Product Key” from the context menu to copy the activation key to the clipboard.
Types of cryptosystems
Essentially, there are two types of cryptosystems based on the way encryption-decryption is performed in the system:
- Symmetric Key Encryption
- Asymmetric key encryption
The main difference between these cryptosystems is the relationship between the encryption and the decryption key. It is logical that in any cryptosystem both keys are closely related. It is almost impossible to decrypt ciphertext using a key that is not related to the encryption key.
Symmetric Key Encryption
An encryption process in which to encrypt and decrypt
information
using the same keys
is called Symmetric Key Encryption.
The study of symmetric cryptosystems is called symmetric cryptography
.
Symmetric cryptosystems are also sometimes called secret-key cryptosystems
.
Some well-known examples of symmetric key encryption methods are Digital Encryption Standard (DES), Triple-DES (3DES), IDEA, and BLOWFISH.
Before 1970, all cryptosystems used symmetric key encryption. Even today its relevance is very high and it is widely used in many cryptosystems. It is unlikely that this encryption will disappear because it has certain advantages over asymmetric key encryption.
The essential features of a cryptosystem based on symmetric key encryption are:
- Individuals using symmetric key encryption must have a shared key before exchanging information.
- It is recommended to change the keys regularly to prevent any attack on the system.
- There must be a reliable mechanism for exchanging keys between communicating parties. Since the keys must be changed regularly, this mechanism becomes expensive and cumbersome.
- In a group of n
person, to provide two-way communication between any two people, the number of keys required for the group is
n × (n - 1) / 2
. - The key length (number of bits) in this encryption is less and hence the encryption-decryption process is faster than asymmetric key encryption.
- The computing power of a computer system required to execute a symmetric algorithm is less.
Individuals using symmetric key encryption must have a shared key before exchanging information.
It is recommended to change the keys regularly to prevent any attack on the system.
There must be a reliable mechanism for exchanging keys between communicating parties. Since the keys must be changed regularly, this mechanism becomes expensive and cumbersome.
In a group of n
person, to provide two-way communication between any two people, the number of keys required for the group is
n × (n - 1) / 2
.
The key length (number of bits) in this encryption is less and hence the encryption-decryption process is faster than asymmetric key encryption.
The computing power of a computer system required to execute a symmetric algorithm is less.
Symmetric key cryptosystem problem
There are two limiting problems with using symmetric key cryptography.
- Setting up the key
- Before any message, both the sender and the recipient must agree on a secret symmetric key. This requires a reliable key establishment mechanism in place.
- The problem of trust
- Because the sender and recipient use the same symmetric key, there is an implicit requirement that the sender and recipient “trust” each other. For example, it may happen that the recipient has lost the key to the attacker and the sender is not informed.
Setting up the key
- Before any message, both the sender and the recipient must agree on a secret symmetric key. This requires a reliable key establishment mechanism in place.
The problem of trust
- Because the sender and recipient use the same symmetric key, there is an implicit requirement that the sender and recipient “trust” each other. For example, it may happen that the recipient has lost the key to the attacker and the sender is not informed.
These two problems greatly hinder modern communication. Today, people must exchange information with unfamiliar and untrusted parties. For example, communication between an online seller and a buyer. These limitations of symmetric key encryption gave rise to asymmetric key encryption schemes.
Asymmetric key encryption
An encryption process in which different keys are used to encrypt and decrypt information
called asymmetric key encryption. Although the keys are different, they are mathematically related and therefore it is possible to obtain the plaintext by decrypting the ciphertext. The process is depicted in the following illustration −
Asymmetric key encryption was invented in the 20th century to come up with the need to share a secret key between people in advance. The significant features of this encryption scheme are as follows:
- Each user in this system must have a pair of dissimilar keys, The secret key
and
public key
. These keys are mathematically related—when one key is used for encryption, the other can decrypt the ciphertext back to the original plaintext. - The requirement is to place the public key in a public repository and the private key as a well-guarded secret. Hence this encryption scheme is also called public key encryption
.
- Although a user's public and private keys are related, it is computationally impossible to find one from the other. This is the power of this scheme.
- When Host1
needs to send data to
Host2,
Host2's
public key from the repository, encrypts the data and transmits. - Host2
uses its private key to extract the plaintext.
- The key length (number of bits) in this encryption is large and hence the encryption-decryption process is slower than symmetric key encryption.
- The processing power of the computer system required to run the asymmetric algorithm is higher.
Each user in this system must have a pair of dissimilar keys, a secret key
and
public key
. These keys are mathematically related—when one key is used for encryption, the other can decrypt the ciphertext back to the original plaintext.
The requirement is to place the public key in a public repository and the private key as a well-guarded secret. Hence this encryption scheme is also called public key encryption
.
Although a user's public and private keys are related, it is computationally impossible to find one from the other. This is the power of this scheme.
When Host1
needs to send data to
Host2,
Host2's
public key from the repository, encrypts the data and transmits.
Host2
uses its private key to extract the plaintext.
The key length (number of bits) in this encryption is large and hence the encryption-decryption process is slower than symmetric key encryption.
The processing power of the computer system required to run the asymmetric algorithm is higher.
Symmetric cryptosystems are a natural concept. In contrast, public key cryptosystems are quite difficult to understand.
You might be thinking, how can an encryption key and a decryption key be "linked" and yet it is impossible to determine the decryption key from the encryption key?
The answer lies in mathematical concepts. It is possible to design a cryptosystem whose keys have this property. The concept of public key cryptography is relatively new. There are fewer known public key algorithms than symmetric ones.
Calling a public key cryptosystem
Public key cryptosystems face one major problem - the user must trust that the public key he uses in communication with a person is really that person's public key and has not been tampered with by a malicious third party.
This is typically achieved through a public key infrastructure (PKI) consisting of a trusted third party. A third party securely manages and verifies the authenticity of public keys. When a third party is asked to provide a public key for any reporting entity X, it is trusted to provide the correct public key.
The third party is satisfied with identifying the user through an attestation process, notarization, or some other process—X is the only or globally unique X. The most common method of providing verified public keys is to embed them. in a certificate digitally signed by a trusted third party.
X.509 Certificates
It so happens that the main “asset” in PKI is the X.509 . A certificate is something like a passport, it contains information that allows you to identify the subject to whom the certificate was issued (the Subject field), indicates who issued it (the Issuer field), the serial number of the certificate, and much more. In Windows, you can manage certificates using the Certificates snap-in (run->certmgr.msc).
Certificate Manager
Certificates are stored in repositories (“Personal”, “Trusted Certification Authorities”, “Trusted Persons”...).
When you receive a certificate, it is important to install it in the correct store. Thus, the certificates that you want to use for electronic signatures must be installed in the “Personal” storage, and the certificates of recipients to whom you will need to send encrypted messages must be installed in the “Trusted Persons” storage. Certification authority (CA) certificates must be installed in the Trusted Root Certification Authorities repository. When installing a certificate, the system offers two options: select the storage automatically or specify manually. I recommend using the second option, since the automation sometimes installs the certificate in the wrong storage. The certificate with which we want to sign messages must have a private key. You can find out about the presence of a private key by looking at the properties of the certificate, where in Russian it will be written in white: “there is a private key for this certificate.”
Private key for the certificate
We can find out the most interesting things about the certificate on the “Composition” tab.
Contents of the certificate
Pay attention to the “Algorithm” and “Public Key” fields. If you want to use the certificate to carry out transactions in Russia, you must see the word “GOST” in all these fields. You should also pay attention to the meaning of the “Key Usage” field and the “Valid from” and “Valid to” fields: the first will allow you to understand whether it is possible to use the certificate to perform the operation we need (encryption, signing), and the second and third - whether it is possible to use a given certificate at a specified point in time. In addition, you should ensure that the certificate is valid. The “Certification Path” tab will help us with this. If everything is fine with the certificate, we will see the inscription: “This certificate is valid.”
Certificate Status
Relationship between encryption schemes
A brief description of the basic properties of the key of two types of cryptosystems is given below −
| Symmetric cryptosystems | Public key cryptosystems | |
| Relationships between keys | Also | Different but mathematically related |
| Encryption key | symmetric | public |
| Decryption key | symmetric | Private |
Due to the advantages and disadvantages of both systems, symmetric key and public key cryptosystems are often used together in practical information security systems.
How to find out your Windows 10 computer ID
The computer ID is the same as the ID of the network card installed in it, since with the help of this card the computer makes all connections to the Internet. You can view your computer’s unique code without third-party programs by following these steps:
- Right-click on the Start icon at the bottom left of the screen.
- Select Device Manager.
- Expand the Network Adapters tree.
- Right-click on your network card and open its properties. The name of the network card is different for everyone, so you shouldn’t use it as a guide.
- Go to the Details tab.
- Expand the “Properties” block and select the “ID or equipment ID” line.
- The “Values” block will contain all IDs related to your PC.
This completes the search for information about the state of Windows and the computer ID. You can always view the activation key through the computer settings if the old one has stopped working or was entered incorrectly. Remember that you only need to activate Windows 10, that is, pay for a license key once. So if your key is no longer accepted by the system, contact the official Microsoft support service.
The product key in Windows 10, as in earlier versions of this operating system, is a 25-digit code consisting of letters and numbers that is used to activate the system. The user may need it during the process of reinstalling the OS, so losing the key is quite an unpleasant event. But if this happens, do not be too upset, since there are ways by which you can find out this code.
There are several programs with which you can view the Windows 10 OS activation key. Let's take a closer look at some of them.
Method 1: Speccy
You need to be careful when using third-party programs, as your product key can be stolen by criminals and used for their own purposes.
Method 3: ProduKey
ProduKey is a small utility that also does not require installation. You just need to download it from the official website, run it and view the necessary information. Unlike other programs, ProduKey is designed only to display activation keys and does not overwhelm users with unnecessary information.
Method 4: PowerShell
You can also find out the activation key using the built-in tools of Windows 10. Among them, PowerShell, the system command shell, occupies a special place. In order to view the desired information, you need to write and execute a special script.
It is worth noting that learning the code using standard tools is difficult for inexperienced users, so using them is not recommended if you do not have enough knowledge in the field of computer technology.
To do this, perform the following sequence of actions.
If, when running the script, you receive a message that script execution is prohibited, then enter the Set-ExecutionPolicy RemoteSigned command, and then confirm your decision with the “Y”
and
Enter
.
Obviously, using third-party programs is much easier. Therefore, if you are not an experienced user, then opt for installing additional software. This will save your time.
The question of how to find out the Windows 10 key may arise in a lot of cases. For example, if you are simply interested in the license code, if you want to transfer activation, etc.
Today, any licensed copy of the operating system from Microsoft has its own unique key, which may indicate that Windows 10 is licensed. How can I find out where such data is stored? In each individual case, it is worth talking about using a different type of confirmation of license acquisition.
For example, when purchasing a laptop that already had the latest version of the OS installed, such data is embedded in the memory of the motherboard. This is done in cases where the manufacturer himself installs the OS. But more often, a PC is purchased that is assembled at some company. Or the parts come home separately, and the user assembles them himself. In this case, the so-called Product Key is used for the operating system.
Here is a small list of such methods:
- Using the extended command line;
- VBS scripts;
- Extract from UEFI;
- ProduKey program;
- Special applications for data collection.
Using special scripts is similar to working with a regular command line. But in this case, it is enough to insert special text into the Notepad document, and then save it in .VBS format - the name itself is not significant here. Perform the rename function and then simply click on the resulting file. These steps will allow you to find out the key for Windows 10, which will simply appear in a separate window on your desktop.
In 64-bit "ten" it is possible to use the extended command line. And in this case, the user will be required to save special text in Notepad, but under the .PS1 extension. Next, launch a command prompt with administrator rights and type “powershell.” In the window, enter the command “SetExecutionPolicy RemoteSigned” and press “Enter”. Then we indicate the path to the previously saved file. In this case, you can find out the Windows 10 key in the “Installed Key” line.
For the same purposes it is possible to use the ProduKey utility. After installation it is easy to work with. It can also be used to determine the number of any office package from Microsoft and other software. ShowKeyPlus works on the same principle and is capable of producing similar results.
To obtain information about the entire PC and about the license in particular, use the applications:
- Everest;
- Speccy and others.
If you still could not find the data, and the PC persistently gives you a message that you need to go through activation, then we recommend either purchasing access again, or using an activator. For example, it copes with its tasks perfectly, even if it is not an official and, at the same time, illegal method. If you know other, more beautiful solutions to this issue, then share them with us in the comments.
A method that works on laptops
The easiest way, but it only works with laptops. You need to turn it upside down. And at the bottom you will find either a sticker or a laser-burned inscription. Most likely, it will indicate the word Windows 10, so you will quickly realize that this is an activation code. However, if you are using an old device, then there may not be such an inscription, and there may only be numbers.
If your device is very old, then there may be a code for a different version. For example, for seven or eight. This is okay - since these codes are also suitable for tens. More problems arise in the case of XP, since such an old version of the OS can no longer be updated to ten, which means its registration data will not work.
We hope that now you know how to find out the Windows 10 activation code and can go through all the procedures without contacting a service center. If all else fails, you can always seek support. Either to our website - write in the comments, or to official Microsoft support. But do the latter only if you know for sure that you purchased the license - separately from the PC, or together with it. Otherwise, you may run into problems.
Previously, if a laptop came with a pre-installed Windows operating system, there was a sticker on the bottom side with a product key or so-called license key. Nowadays these stickers are not put on laptops and it is no longer possible to simply find out the product key for them.
But, if you use some tricks, you can still find out the Windows 10 product key. In this material we will look at several ways to do this.
It should be noted right away that different methods extract keys from different sources, so the resulting keys will differ. So, the key extracted from the operating system will be different from the key that is extracted from the UEFI motherboard.
How to make an open-end wrench with your own hands?
For those who decide to make this instrument themselves, there are some small recommendations. You need to start manufacturing using a sample of a ready-made similar product. Complete a drawing of the required product, taking into account which you will make your key.
First, we make a blank from a steel sheet with a size several millimeters larger than the external size of the sides of the finished product. There are difficulties with thick instruments
. You shouldn't cut it out with a hacksaw. And choosing a gas torch as a cutting tool is contraindicated. It is advisable to use forging in the process. This can be done by flattening a metal rod.
Then, when the workpiece is ready, we begin to make markings. If the workpiece does not have very smooth edges, then it is advisable to file them down to remove scale. Afterwards you need to apply paint
onto the treated surface. You can use quick-drying varnish or paint. Applying the sample is done after the paint has completely dried. It is advisable to use some kind of press to prevent the sample from slipping when delineating.
The scriber is a metal sharpened wire. Then the final marks must be placed on the separation of the workpiece and the sample, retreating a few millimeters from those already made, and then marking them. First, place the core at the risk with an inclination, and level it when striking with a hammer. The step between the pits in the pharynx should be 4–5 mm.
Then we drill out the throat. You can use an electric drill with drills with a diameter of 5–6 mm. The drill should not get too hot. You can cool it in water. Then, when you make the second shed, you need to remove the excess.
Well, at the end you need to harden the part. At home, this can be done using gas. If you use a special stove or forge
– it will be perfect. To remove the product, use pliers by lowering the key into the water. It is necessary to remove and immerse until the sponges completely darken. This is the technology for making an open-end wrench.
Almost every man, even if he lives not in a private house, but in an ordinary apartment, must have open-end and ring wrenches. You never know what can happen in a household. This is especially true when you have your own transport or often have to deal with equipment. When you know that you have a set of spanners, you don’t have to worry about how to make urgent repairs if necessary or replace a long-worn part yourself. However, sometimes when purchasing such a tool, difficulties arise with the choice. Therefore, let’s look at what it is like, and what you should pay attention to.
Socket wrenches: what is their advantage?
Have you ever unscrewed an old rusty bolt? If you use a regular open-end wrench for this, which in its shape resembles the letter U, then you can easily ruin the edges of the fastener, and then you will have to struggle with pliers and a chisel. Such situations happen quite often if the size of the tool used is slightly larger than necessary. In such cases, especially when the fasteners have good access from all sides, it is much better to use spanners. Their working profile allows you to tightly cover the part, completely repeating its outline, and not worry about the integrity of the edges. This ability allows the master to exert great effort, so it is easy to unscrew or tighten bolts or nuts with this tool.
Spanners: features and main types
As a rule, this type of instrument is made double-sided. The handles of such keys can be either straight or curved. They must be used in accordance with the parameters of the nut, otherwise there is a risk of the teeth abrading, which leads to damage to the tool. Socket wrenches are good for everyone, except for one drawback: the mandatory availability of free access to the fasteners. This is their only weakness. If a horn instrument can still be used somehow from the side, then such a number will not work with a cap instrument. And yet, the latter is much more convenient to work with, which is why it is very popular among both home craftsmen and professionals. The profile of the socket wrench heads can contain either six (TORX profile) or twelve edges.
The greater their number, the smaller the angle required for turning and the more convenient it is to work in tight spaces. But hex keys have better contact with the nut. Therefore, with them you don’t have to worry about smearing the corners of the fasteners. The ring and the handle can be located either in the same plane or at a slight angle of inclination (15°). Tools of the second type are more universal, while the first type is almost never used. The most interesting options are those with an S-shape, a hinge or a ratchet (ratchet). The first two allow you to reach nuts in hard-to-reach places, thereby eliminating the advantage of open-end nuts. A spanner wrench with a ratchet allows you to completely forget about the need to re-throw it after each turn. Another important advantage is the small angle of rotation required to tighten/unscrew the nut. The number of teeth in the ratchet can be up to 72. In this case, the rotation angle required is only 5°.
Wrenches are used to work with bolted connections. They come in several varieties, each of which is used for specific purposes. The choice of tool configuration depends on the difficulty of accessing the threaded connection. If it is in an open place, then any wrench will do, but if you need to dodge, then you need a special shape of the tool.
Types of wrenches
First of all, the instrument differs in size. Each one is designed for a specific hex nut. The size of the key is indicated by numbers that correspond to the diameter of the landing throat in millimeters. Foreign instruments may have an inch designation, but they are practically not used in the CIS.
There are more than 10 types of wrenches, which are divided into the following groups:
- Monolithic.
- Adjustable.
- Composite.
- With a special profile.
You can also note special keys, but they are used very rarely and only in special designs. Most of these tools are almost never used, so they can be ignored.
Monolithic wrench
A monolithic wrench is a solid metal structure. This tool is the most common. It is mainly made from special steel, which contains chromium and vanadium. The monolithic type is divided into several subtypes:
- Rozhkovy.
- Cap.
- Tortsevoy.
- Combined.
Rozhkovy
The horn tool is used for nuts and bolts ranging in size from 3.6 to 95 mm. This is the most common key that is used in all areas, including car servicing. Its design is a flat profile, at the end of which there are two axes for covering the heads of threaded connections. The horn instrument can be single-sided or double-sided.
Single-sided has horns on one side only, while the other is a cut profile. Often, when working on a tightly clamped connection, a tube can be placed on the other end of the wrench to increase the leverage and make it easier to unscrew. A double-ended wrench has horns on all ends. They are usually designed for nuts of different diameters.
Thanks to their flat design, open-end wrenches are quite compact. The direction of their jaws has a deviation of 15 degrees. This reduces the risk of slipping and adds additional maneuverability. The disadvantage of the horn design is the flimsiness of fixing the joints. When unscrewing with strong force, abrasion of the metal on the edges of the bolts is observed. In addition, the horns may break off or expand.
Cap
The box spanner has sizes from 6 to 55 mm. Its working part is a ring with edges, which ensures complete crimping of nuts and bolts. When working with such a tool, the risk of edge licking is eliminated. The cap design can also be one-sided or two-sided. The single-sided variation includes tools ranging in size from 30 to 55 mm. The disadvantage of the slip-on type is the need for open access to the threaded connection. If the nut is only a few millimeters away from the obstacle, then it will not be possible to fix the key on it.
Tortsevoy
The working part of such a tool is a tube with an internal notch for fixing the edges. The wrench is used to loosen deep seated bolts and nuts. The reliability of fixation corresponds to the slip-on type. Depending on the shape, there are tubular, “T” and “G” shaped. The first are a straight tube, with ends fitted to the edges and a small through hole in the center, which are used to thread a pin through, making rotation easier. Such keys are called spark plugs because they are used to change spark plugs in internal combustion engines. “T” and “L” shaped keys have 6 or 12 edges. Their curved shape is tailored to specific working conditions.
Combined
This double-sided tool has an open-end wrench and a spanner on each end. Available in sizes from 5 to 32 mm. The option of the same or different sizes of open-end and ring wrenches is possible. Such a tool is often included in standard kits for servicing motorcycles and other small equipment.
Adjustable type
An adjustable wrench is a more advanced, but not as reliable design as a monolithic one. It can change the size of the girth of the working part, so it is suitable for a wide range of nuts and bolts. There are several subtypes of adjustable tools:
- Divorceable.
- Pipe.
- Repositionable.
- French.
Adjustable
The adjustable one resembles the carob one, but is more massive. Its special feature is its sliding jaws. This tool is universal. It allows you to work with non-standard nut sizes. Changing the working width is done with a simple worm-type adjuster. Such a tool fixes only two edges, so it can lick off the nuts. It should not be hit with a hammer as the worm adjuster may jam and bend, making further attempts to adjust the width impossible.
Pipe
A pipe wrench is a universal tool. It comes in 5 sizes, with a coverage range from 0 to 120 mm. Adjustment is made using a clamping nut on one of the handles. The edges are grabbed by two jaws like a lever. The tighter you press it, the more secure the fixation will be. There are several options for lip shapes. There are flat and rounded. The former work with regular nuts, while the latter can grip round joints.
Perestavnaya
The adjustable wrench also provides grip via a lever system. To work with it, you need to use strong force, since its design is more primitive than a pipe one. The surface of the adjustable mechanism is serrated, which ensures tighter contact between the two handles. There is also a notch on the lips. It increases the reliability of the contact of the horns to the surface of the edges.
French
The French wrench is a very old design. Despite this, it can be found in the tool kit of many car enthusiasts and mechanics. The French design was invented back in the 18th century. Since that time, the principle of adjusting the tool has changed slightly. It should be noted that such keys suffer from the presence of backlashes, which complicates the reliable fixation of the jaws. They do not tolerate impacts, so if the nut does not budge, it is best to use a tube to increase leverage.
Composite type
The compound type is socket heads. On one side they have 6 or 12 edges for fixing the nuts, and on the second 4 edges for holding the wrench. When assembled, the composite key repeats the design of a conventional socket type. The advantage of the heads is that they are fitted to one driver. Thus, a whole set of end caps and one handle can fit in a small box. At the same time, it will present all the popular sizes that are required for work.